Setting up SSO with Azure AD
This guide walks you through the setup process for enabling Single Sign-On (SSO) for your instance with Microsoft Azure Active Directory (Azure AD). Once the SSO is configured for your instance, users will be redirected to your configured Azure AD identity provider to complete the login.
We support SSO login to cptn.io instance using OAuth/OpenID Connect (OIDC).
Setup Instructions
In cptn.io instance
- Login to your cptn.io instance.
- Navigate to Settings page from left nav.
- Click Single Sign-On tab on the page.
- A SSO Configuration page will be displayed.
- Copy the Redirect URI shown for your instance. This URL will be used for defining configuration in your identity provider.
In Azure Portal
Create App Registration
- Login to https://portal.azure.com
- In the top search menu, search for App registrations.
- Click App registrations from the list shown.
- Click New registration button on the page.
- Provide a name for the application. E.g. cptn.io - Dev Team
- Select Accounts in this organizational directory only
- Under Redirect URI, Select Web from the Select a Platform dropdown
- Provide the copied OAuth Redirect URI as the Redirect URI.
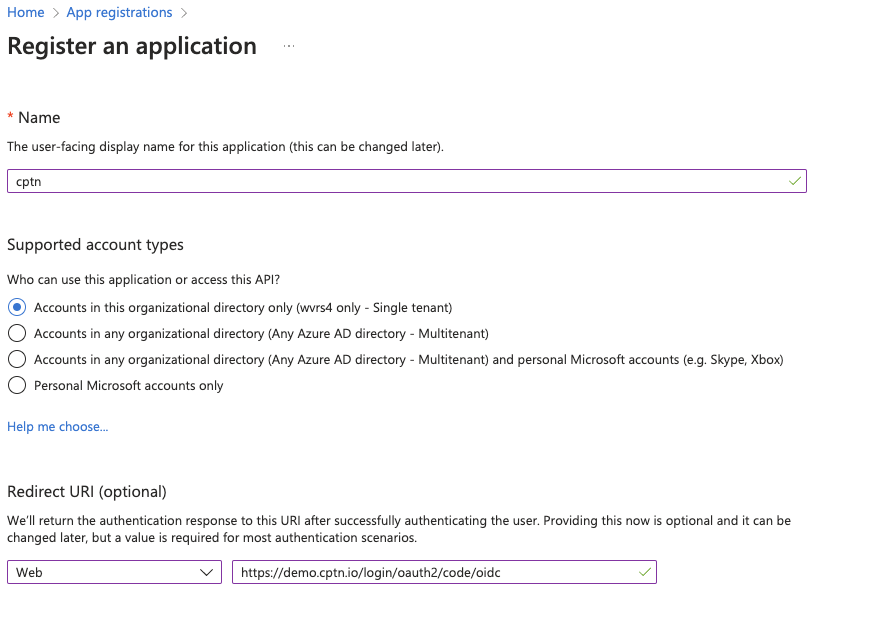
- Click Register
- A new App registration will be created.
Configuring Authentication Properties
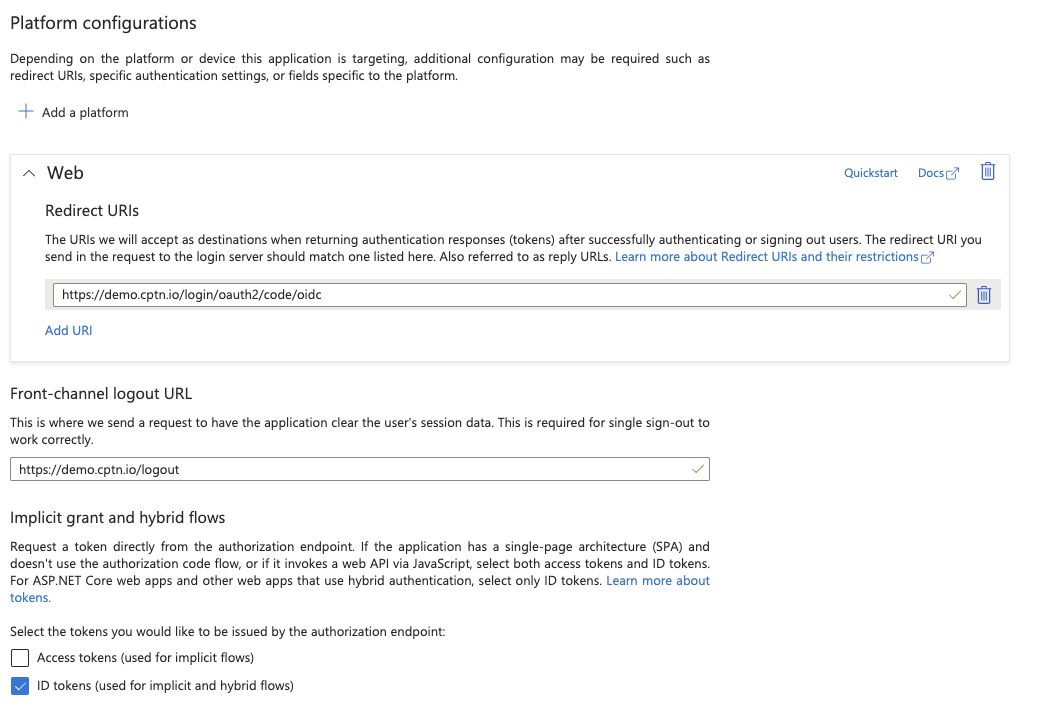
- Click Authentication in the left nav menu.
- Provide
https://${your-cptn-instance-url}/logoutas Front-channel logout URL. - Select ID tokens (used for implicit and hybrid flows) under Implicit grant and hybrid flows section.
- Click Save
Configuring Permissions
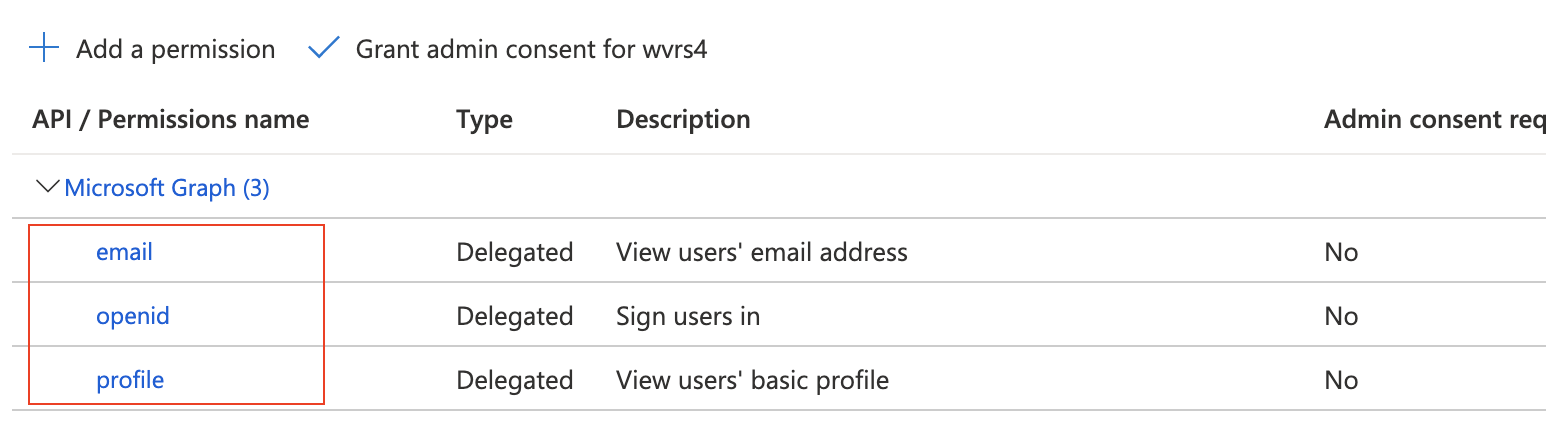
- Click API Permissions from the left nav menu.
- Remove User.Read permission if it's already available in the list of API/Permissions names.
- Click Add a permission button.
- A new fly-in page will be displayed. Click Microsoft Graph tile.
- Click Delegated permissions tile.
- Select Openid, email, profile from the list of permissions.
- Click Add permissions
Creating a Client Secret.
- Click Certificates & secrets from the left nav menu.
- Click New client secret button.
- Provide a name for the secret and select an appropriate Expires interval. Note that, you must generate a new client secret and update your SSO configuration in your cptn instance before the expiry of this secret.
- Copy the generated Value of the client secret. This is the value to be used as Client Secret below.
- Click Overview from the left navigation menu.
- Copy Application (client) ID value. This is the value to be used as Client ID below.
- Click Endpoints button.
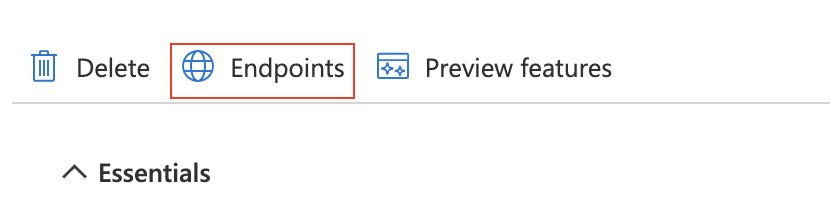
- A fly-in page will be displayed.
- Copy the url for OpenID Connect metadata document. This url ends with /.well-known/openid-configuration
Back in cptn.io instance
- Login to your cptn.io instance.
- Navigate to Settings page from left nav.
- Click Single Sign-On tab on the page.
- A SSO Configuration page will be displayed.
- Provide the Client ID copied from Azure portal
- Provide the Client Secret copied from Azure portal.
- Provide OIDC Configuration Well-Known URL for your Azure AD domain.
- Click Save Changes.
The SSO configuration is now complete. You can now logout and try logging using your SSO credentails.
note
Once you confirm that the SSO based login is successful, remember to update the SSO configuration to set Allow login only with SSO to ON to disable Password-based login to your instance.